Windows 主机入侵排查和应急响应 2024-10-06 12:26:38 Steven Xeldax > 既然已经写了linux的应急响应,想了下还是把mac和windows的也补一下,本文的主要内容都是对目前有的入侵排查、应急响应以及取证的一些SOP汇总。用于笔记记录备忘 linux 应急响应(https://xeldax.top/article/linux_incident_response mac 应急响应 (https://xeldax.top/article/macos_incident_response) [TOC] 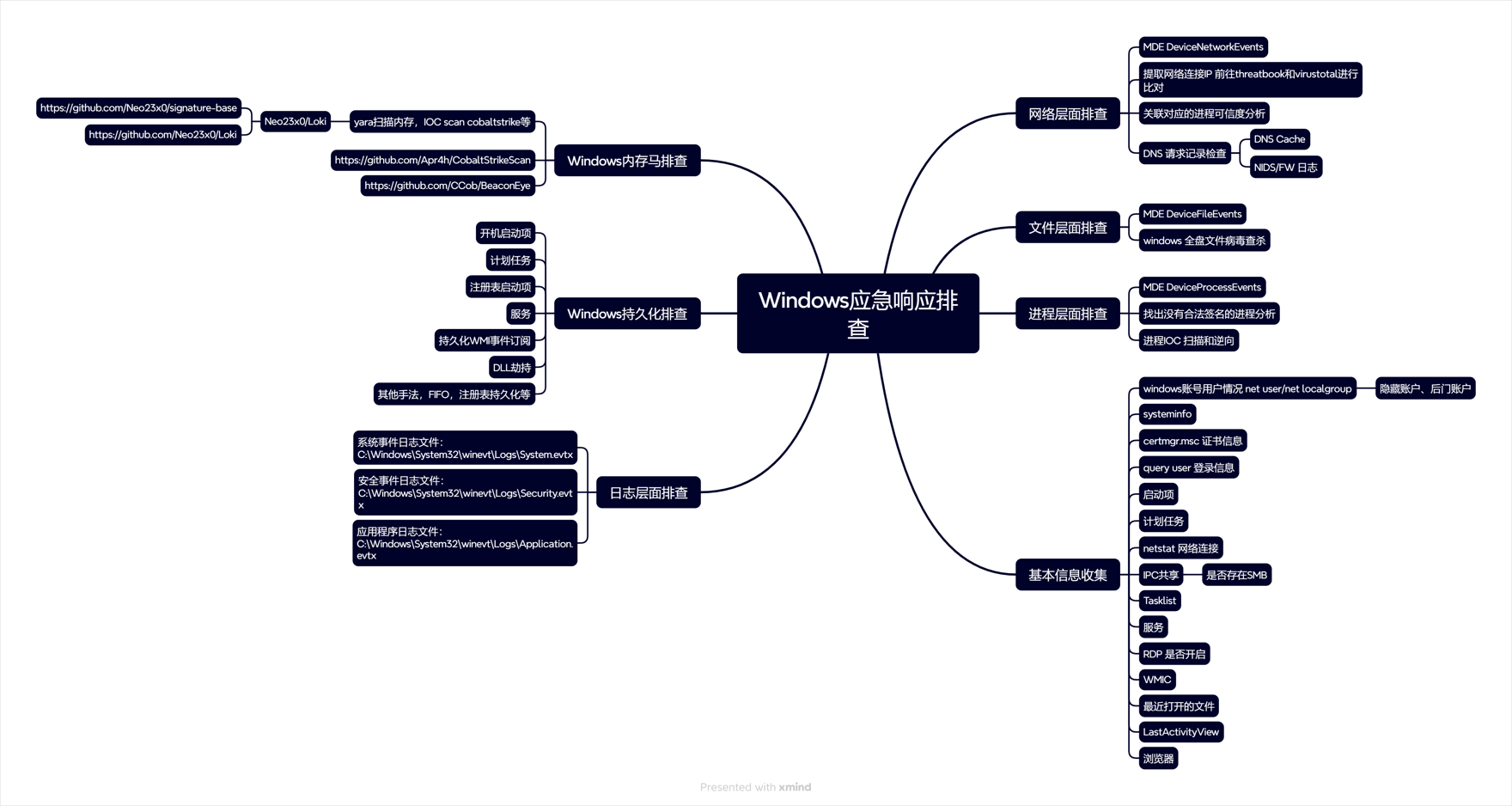 # windows 主机入侵排查 关于入侵排查首先可以从表现上进行初步评估,确认是否存在入侵的迹象。常见的入侵迹象包括但不限于: - 系统性能异常,如 CPU、内存使用率突然升高。 - 不明进程或服务运行。 - 文件或目录被篡改或新增。 - 网络流量异常,如大量未知的外部连接。 - 各种安全设备的告警 我们可以从这些异常详细中突破发现某个可疑的目标,比如高CPU下可疑的进程,可疑的文件等等,但有时候没有任何痕迹现象可能就是需要去评估某一台windows主机是否被入侵过,这种就需要从各个角度逐一进行检查,例如: - 文件扫描:检查是否存在恶意文件、可疑文件 - 进程排查:检查是否存在恶意进程例如C2,木马病毒,后门,downloader等 - 网络检查:检查是否存在可疑外联或者大量网络请求扫描内网 - 内存扫描:检查是否存在IOC 内存指标 - windows持久化:检查是否存在不是管理员添加的持久化任务,这种往往是攻击者为了驻留权限遗留的 - windows日志痕迹检查:从windows event log中找到是否存在可疑记录,例如爆破登录,大量失败记录等,往往是遭受red team攻击的痕迹 # windows 主机应急响应 ## 恶意DNS请求 1.dns sec 设备检测到恶意DNS请求或者dns tunnel 2.结合告警日志定位IP以及主机 3.前往主机定位具体哪个进程,可以通过MDE DeviceNetworkEvents进行判断,如果无法判断可以运行脚本持续查看进程,如下所示: ``` @echo off :loop if exist "%USERPROFILE%/Desktop/bat_result.txt" ( echo "find it!!!" timeout /T 5 /NOBREAK goto loop ) else ( for /f "tokens=5" %%a in ('netstat /ano ^| findstr 123.123.123.123') do ( wmic process where processid=%%a get name,executablepath,processid,CommandLine >> %USERPROFILE%/Desktop/bat_result.txt ) timeout /T 1 /NOBREAK ) gotoloop ``` 或者安装sysmon监听dns事件,sysmon dns事件可以精确到哪个进程 4.查看该进程的来源已经上下文调用 5.清理该进程以及持久化 ## 木马病毒/恶意文件 其他见NOP Team的应急响应手册 # 应急响应cheatsheet速查 ## DFIR powershell:Incident-Response-Powershell https://github.com/Bert-JanP/Incident-Response-Powershell 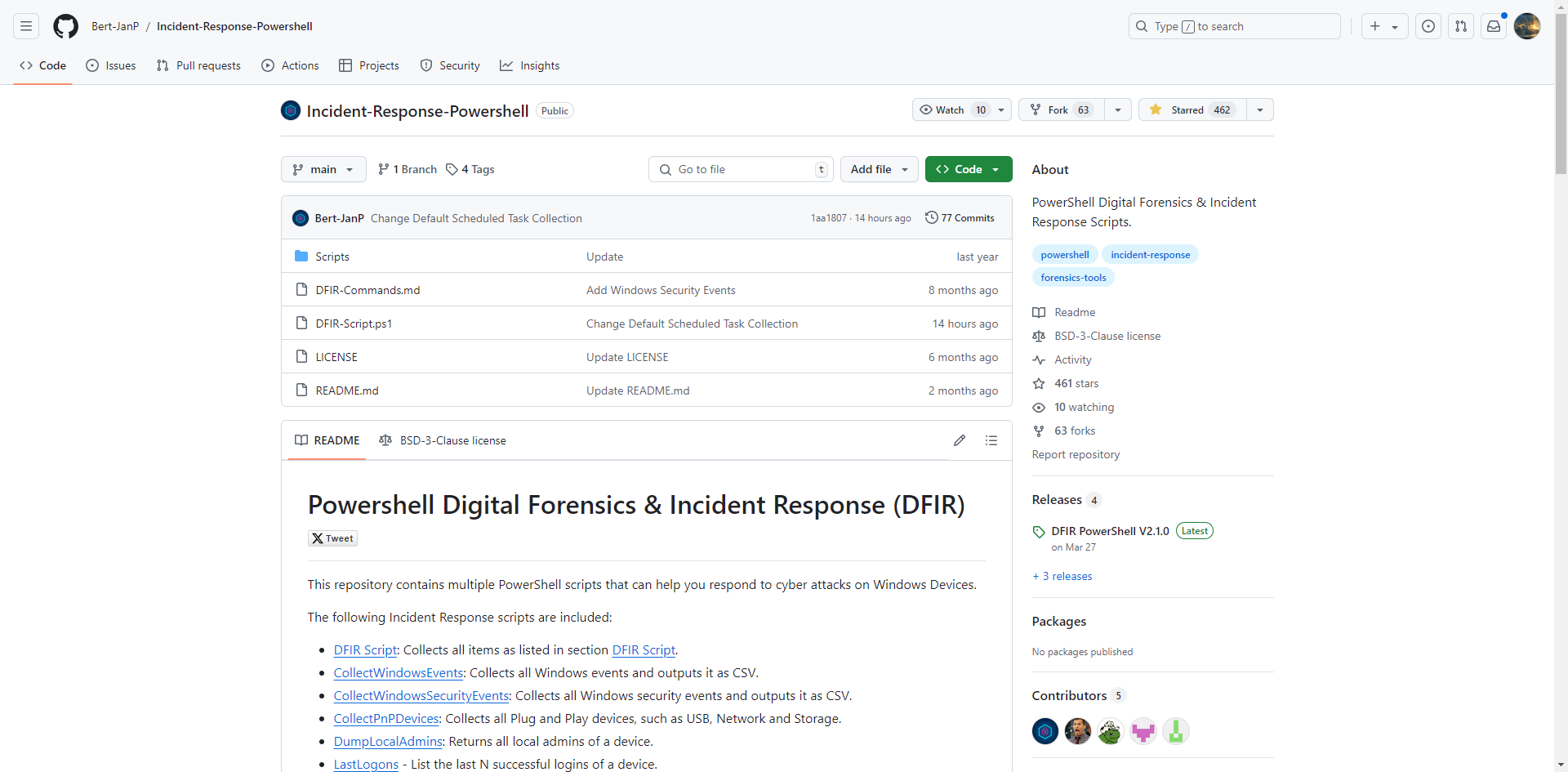 ``` Powershell.exe -ExecutionPolicy Bypass .\DFIR-Script.ps1 ``` 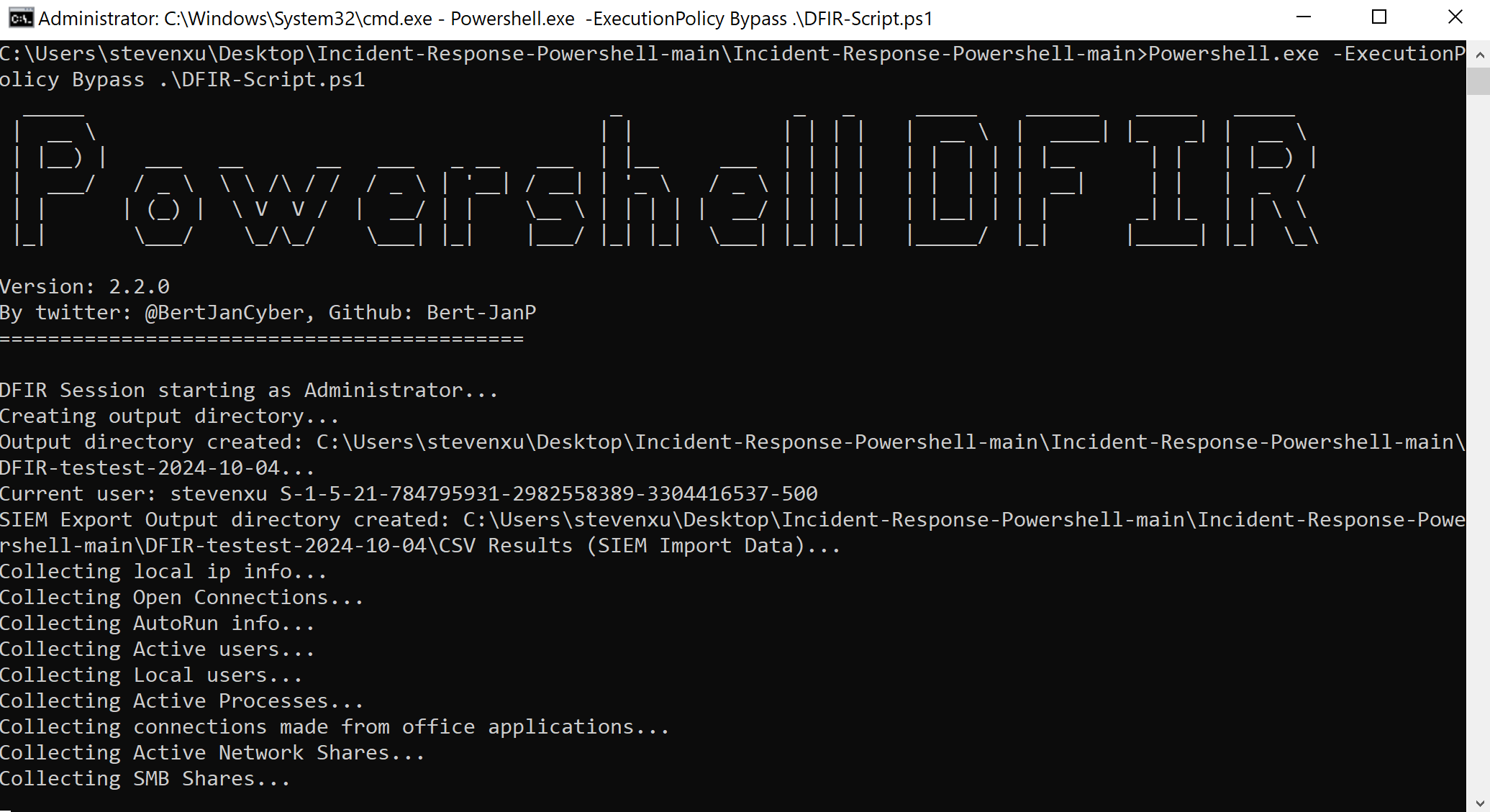 生成的CSV Results可以导入到splunk平台或者是sentinel平台,以便于我们在SIEM平台上进行分析 ``` https://kqlquery.com/posts/incident-response-powershell-v2/ ``` ## Blue-Team-Notes https://github.com/Purp1eW0lf/Blue-Team-Notes 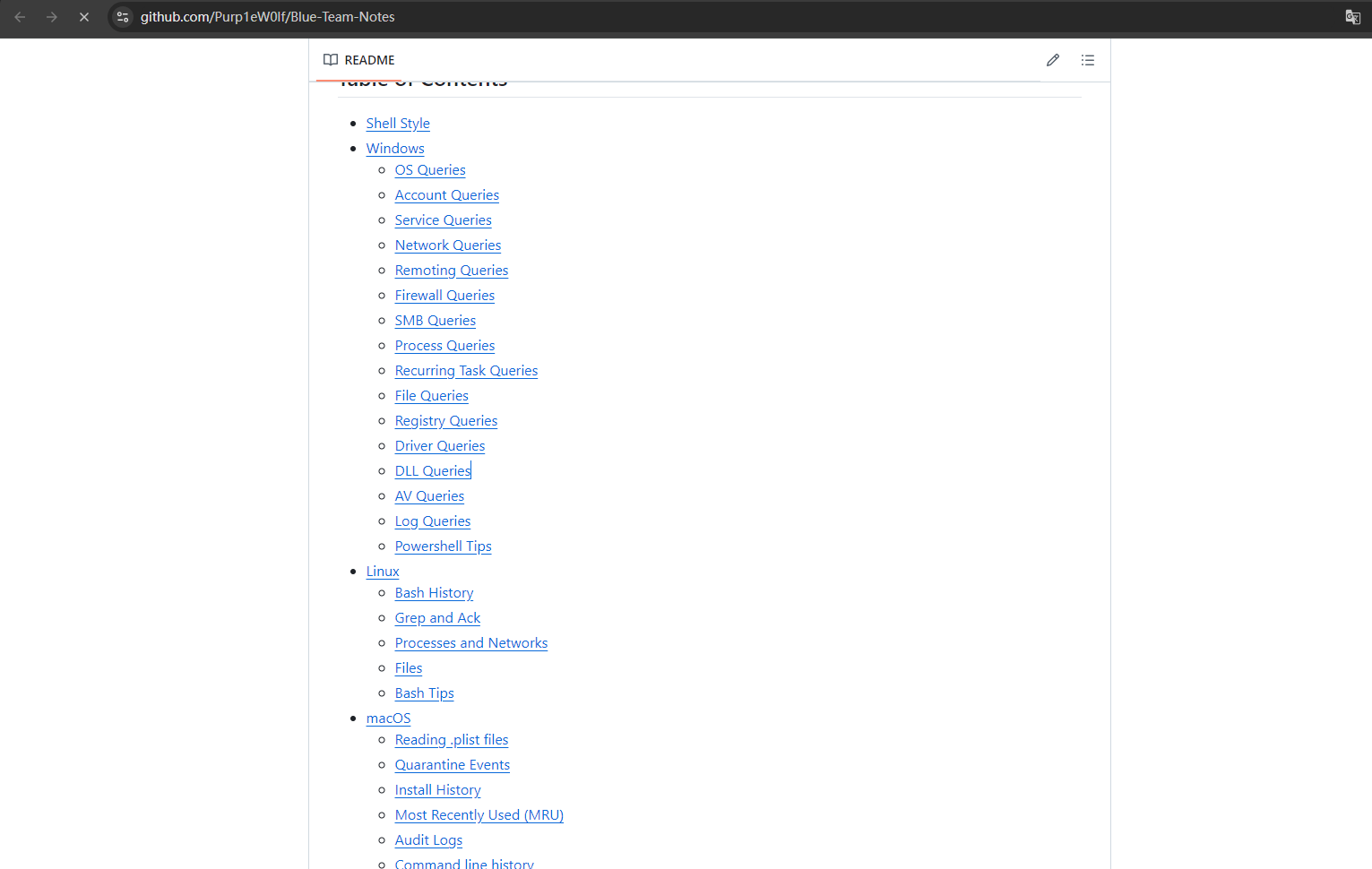 ## KAPE https://zgao.top/%E4%BD%BF%E7%94%A8kape%E8%87%AA%E5%8A%A8%E5%8C%96%E9%87%87%E9%9B%86%E5%B9%B6%E5%88%86%E6%9E%90windows%E5%8F%96%E8%AF%81%E6%95%B0%E6%8D%AE/  Run as administrator  勾选上 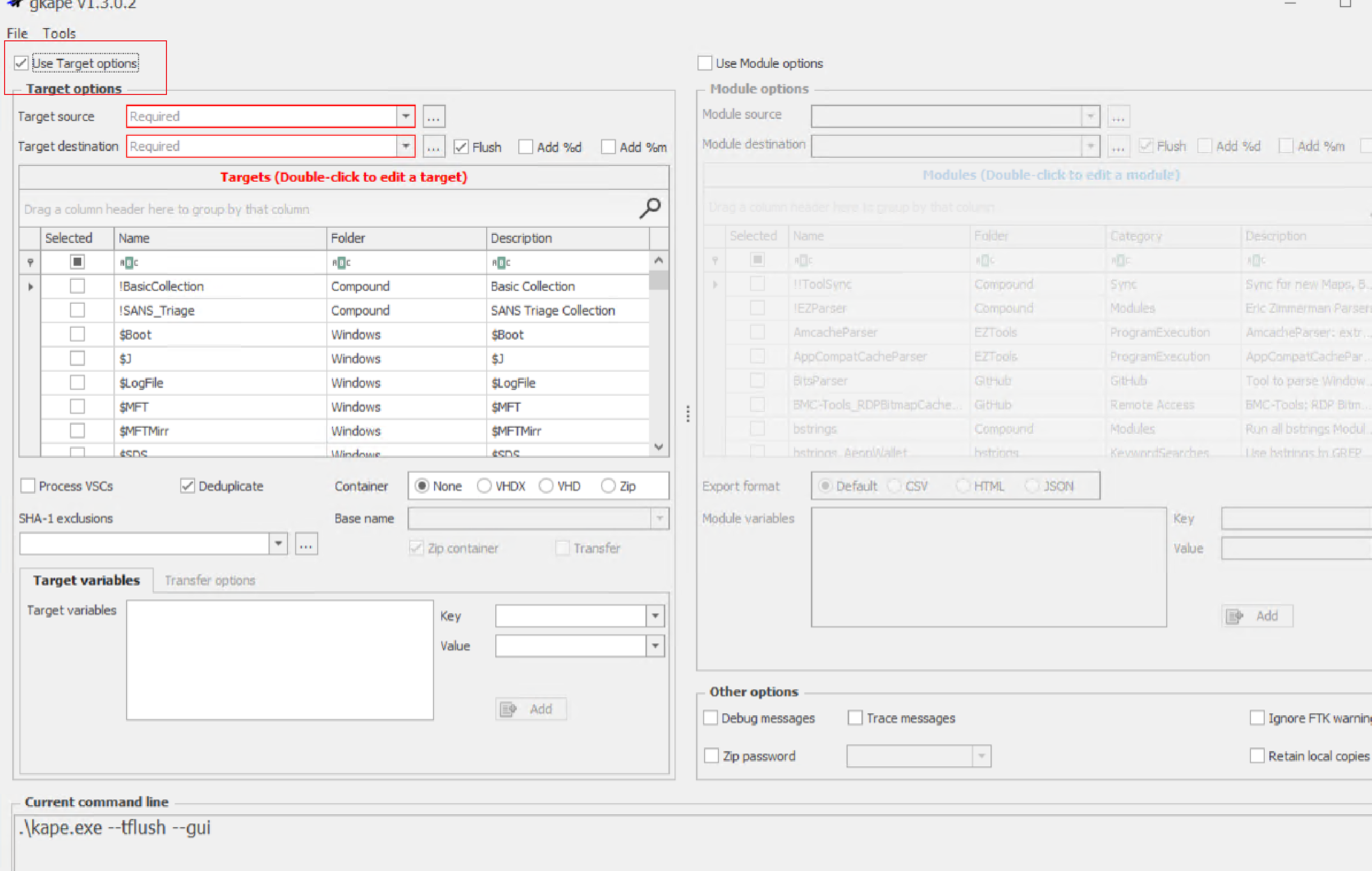 按照教程选择好点击execute即可 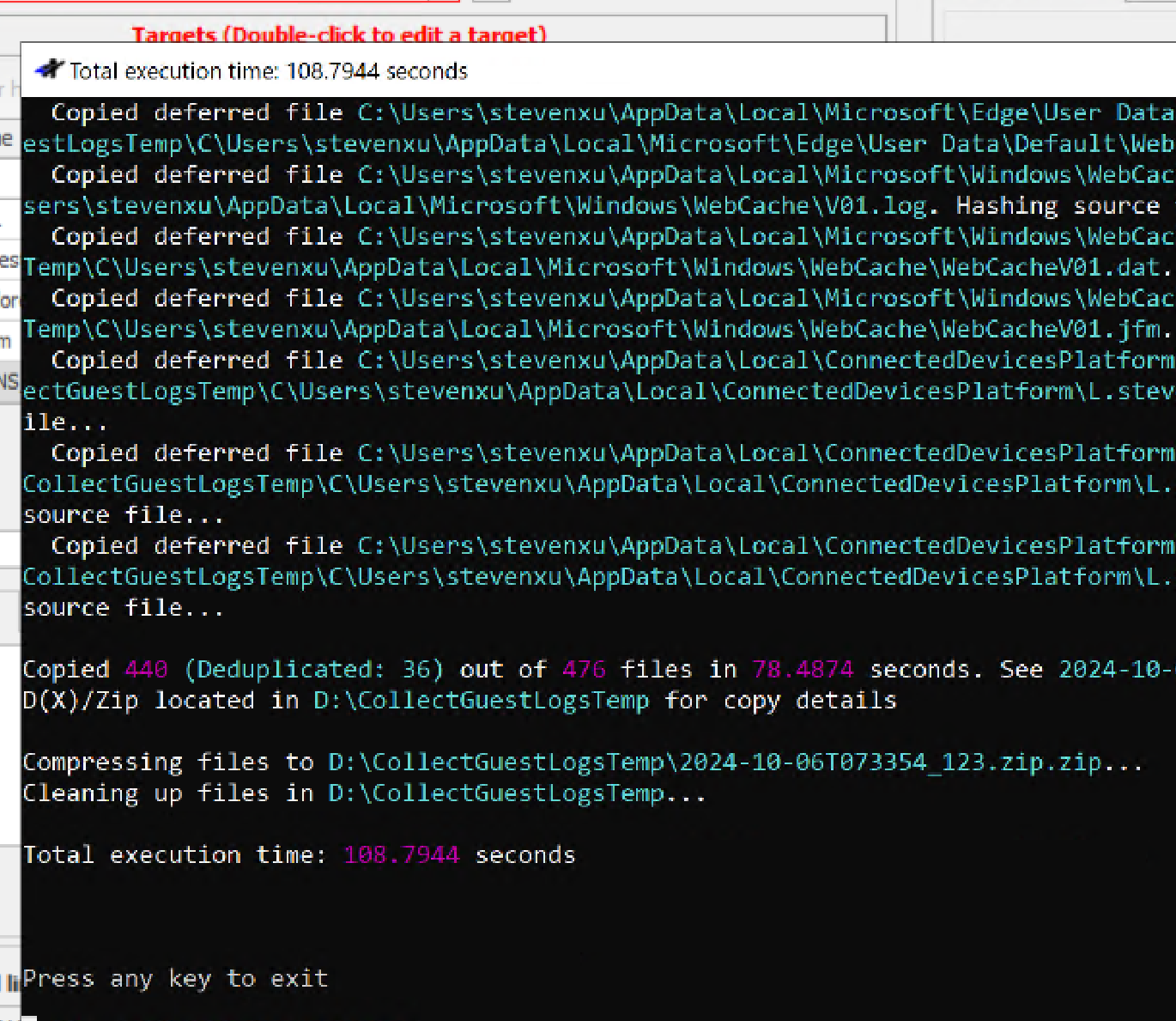 也可以直接使用cmd ``` .\kape.exe --tsource C: --tdest D:\CollectGuestLogsTemp --tflush --target !BasicCollection,!SANS_Triage --zip 123.zip ``` ## windows-forensic-artifacts https://github.com/Psmths/windows-forensic-artifacts/tree/main  ## https://github.com/Yamato-Security hayabusa https://mahim-firoj.medium.com/incident-response-and-threat-hunting-using-hayabusa-tool-383da273183a hayabusa是一个利用sigma规则去扫描我们目标windows机器上的windows日志的工具,我们可以利用这个工具去初步判断分析windows log中的一些异常。  hayabusa-2.17.0-win-x64.exe computer-metrics -l 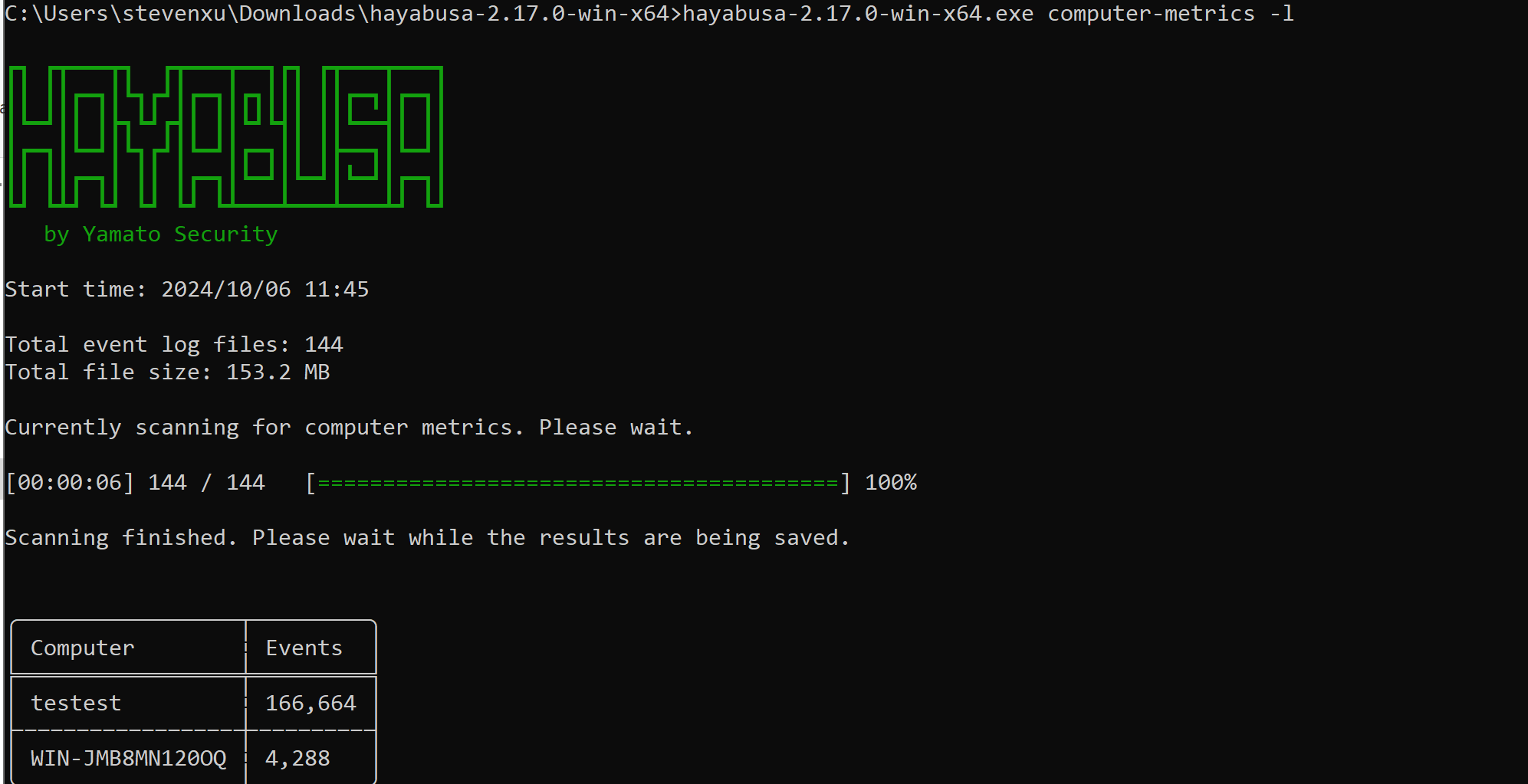 hayabusa-2.17.0-win-x64.exe csv-timeline -l -H 1.html --output 1 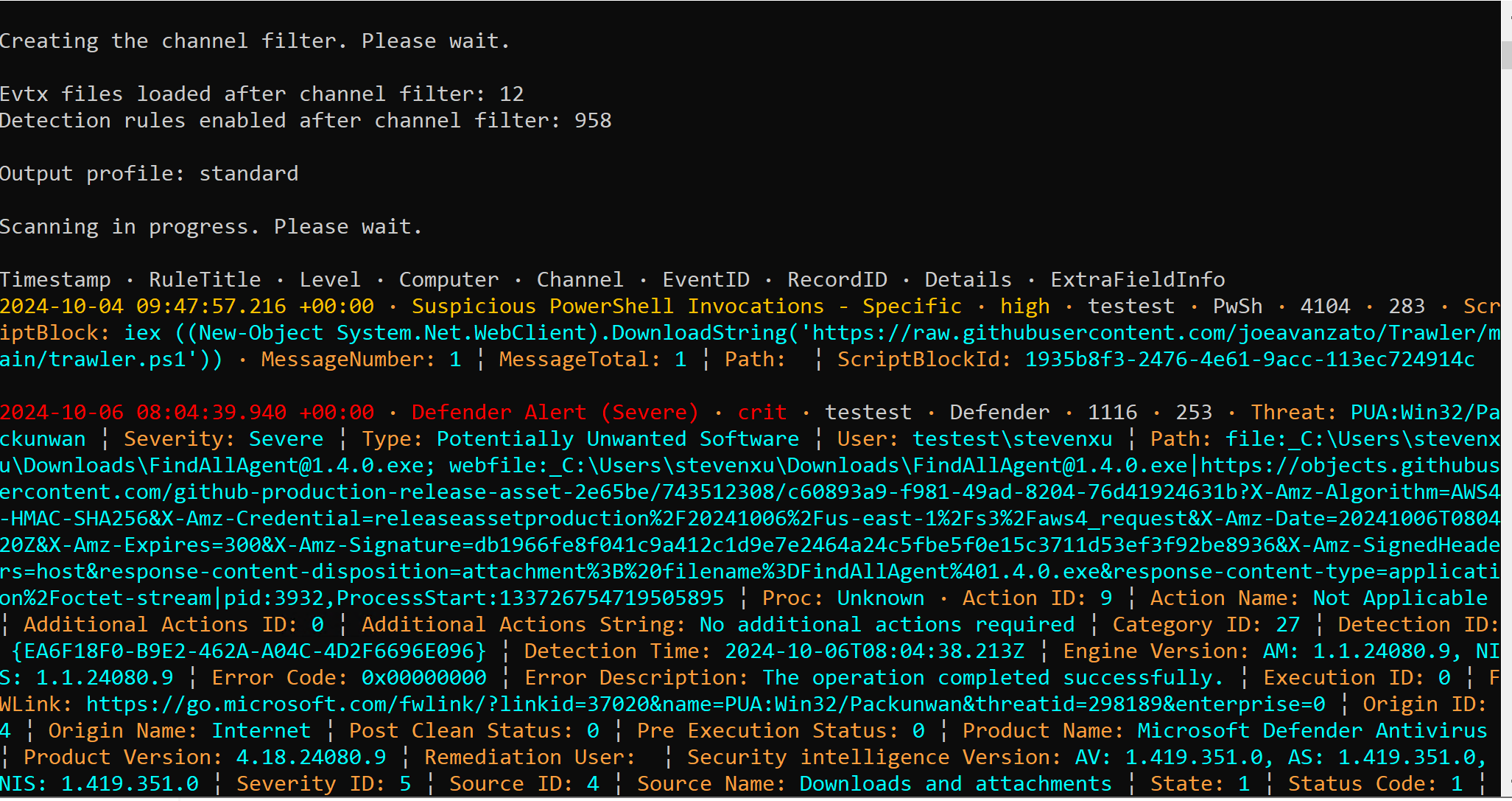 hayabusa-2.17.0-win-x64.exe logon-summary -l 查看登录信息 ## lastactivity 工具下载地址:https://www.nirsoft.net/utils/computer_activity_view.html LastActivityView 工具的日志源主要来自于 Windows 操作系统中的各种日志,包括但不限于以下几种: 事件日志:工具会访问 Windows 系统的事件日志,如系统事件日志、安全事件日志、应用程序事件日志,以提取包含用户活动信息的事件记录。 注册表:工具可能会扫描 Windows 注册表中的特定项,以获取关于最近活动的信息,例如最近打开的文件、最近访问的文件夹等。 其他系统记录:除了事件日志和注册表,工具可能会解析其他系统记录,如用户活动日志、网络连接日志等,以获取用户活动信息。 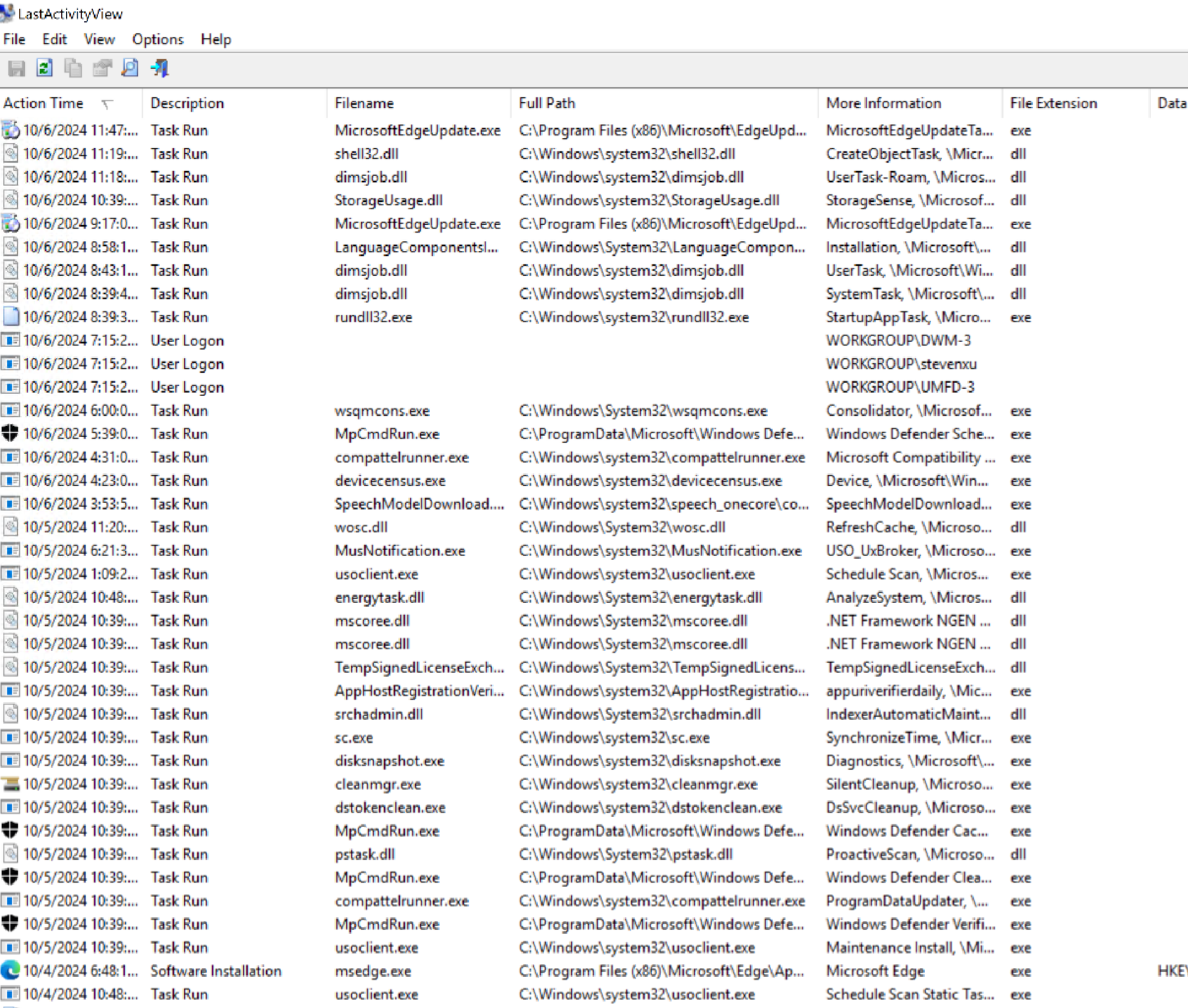 ## IOC 扫描:clamAV和Loki clamAV进行杀毒扫描,loki进行yara IOC匹配。 clamAV下载地址: https://www.clamav.net/downloads#otherversions https://docs.clamav.net/ 复制配置文件,删除example字符 copy .\conf_examples\freshclam.conf.sample .\freshclam.conf copy .\conf_examples\clamd.conf.sample .\clamd.conf write.exe .\freshclam.conf write.exe .\clamd.conf 更新病毒库 freshclam.exe 内存扫描 # clamscan.exe --memory 扫描文件 clamscan.exe -r d: ``` C:\Users\X\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64>write clamd.conf C:\Users\X\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64>write freshclam.conf C:\Users\X\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64>freshclam.exe Creating missing database directory: C:\Users\steven\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64\database ClamAV update process started at Sun Oct 6 20:51:37 2024 daily database available for download (remote version: 27419) Time: 8.3s, ETA: 0.0s [========================>] 61.20MiB/61.20MiB Testing database: 'C:\Users\steven\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64\database\tmp.fbd4356936\clamav-3a6ead1e2d865502c8db30d172f55b33.tmp-daily.cvd' ... Database test passed. daily.cvd updated (version: 27418, sigs: 2067197, f-level: 90, builder: raynman) Received an older daily CVD than was advertised. We'll retry so the incremental update will ensure we're up-to-date. daily database available for update (local version: 27418, remote version: 27419) Current database is 1 version behind. Downloading database patch # 27419... Time: 0.3s, ETA: 0.0s [========================>] 778B/778B Testing database: 'C:\Users\steven\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64\database\tmp.fbd4356936\clamav-ac5e29bacbba1e6bc5043d6baf97984f.tmp-daily.cld' ... Database test passed. daily.cld updated (version: 27419, sigs: 2067197, f-level: 90, builder: raynman) main database available for download (remote version: 62) Time: 21.8s, ETA: 0.0s [========================>] 162.58MiB/162.58MiB Testing database: 'C:\Users\steven\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64\database\tmp.fbd4356936\clamav-c4a59cc5172b87ac8c4ad9704ef15d95.tmp-main.cvd' ... Database test passed. main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr) bytecode database available for download (remote version: 335) Time: 0.5s, ETA: 0.0s [========================>] 282.94KiB/282.94KiB Testing database: 'C:\Users\steven\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64\database\tmp.fbd4356936\clamav-58bb245b1c82cb2868de142d9618260f.tmp-bytecode.cvd' ... Database test passed. bytecode.cvd updated (version: 335, sigs: 86, f-level: 90, builder: raynman) C:\Users\X\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64> C:\Users\X\Downloads\windows应急响应工具包\clamav-1.4.1.win.x64>clamscan -r "D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs" Loading: 16s, ETA: 0s [========================>] 8.70M/8.70M sigs Compiling: 3s, ETA: 0s [========================>] 41/41 tasks D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\Assessor-GUI_error.log: OK D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\gui_20241003_140853.log: OK D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\gui_20241003_154202.log: OK D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\gui_20241003_154630.log: OK D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\gui_20241004_154037.log: OK D:\Tools\CIS-CAT Lite Assessor v4.46.0\Assessor\logs\GUI_logs\gui_20241004_154728.log: OK ----------- SCAN SUMMARY ----------- Known viruses: 8698995 Engine version: 1.4.1 Scanned directories: 1 Scanned files: 6 Infected files: 0 Data scanned: 2.84 MB Data read: 1.41 MB (ratio 2.02:1) Time: 19.392 sec (0 m 19 s) Start Date: 2024:10:06 21:00:39 End Date: 2024:10:06 21:00:59 ``` loki下载地址: https://github.com/Neo23x0/Loki/releases/tag/v0.51.0  更新 loki --updatge 运行 直接运行loki即可 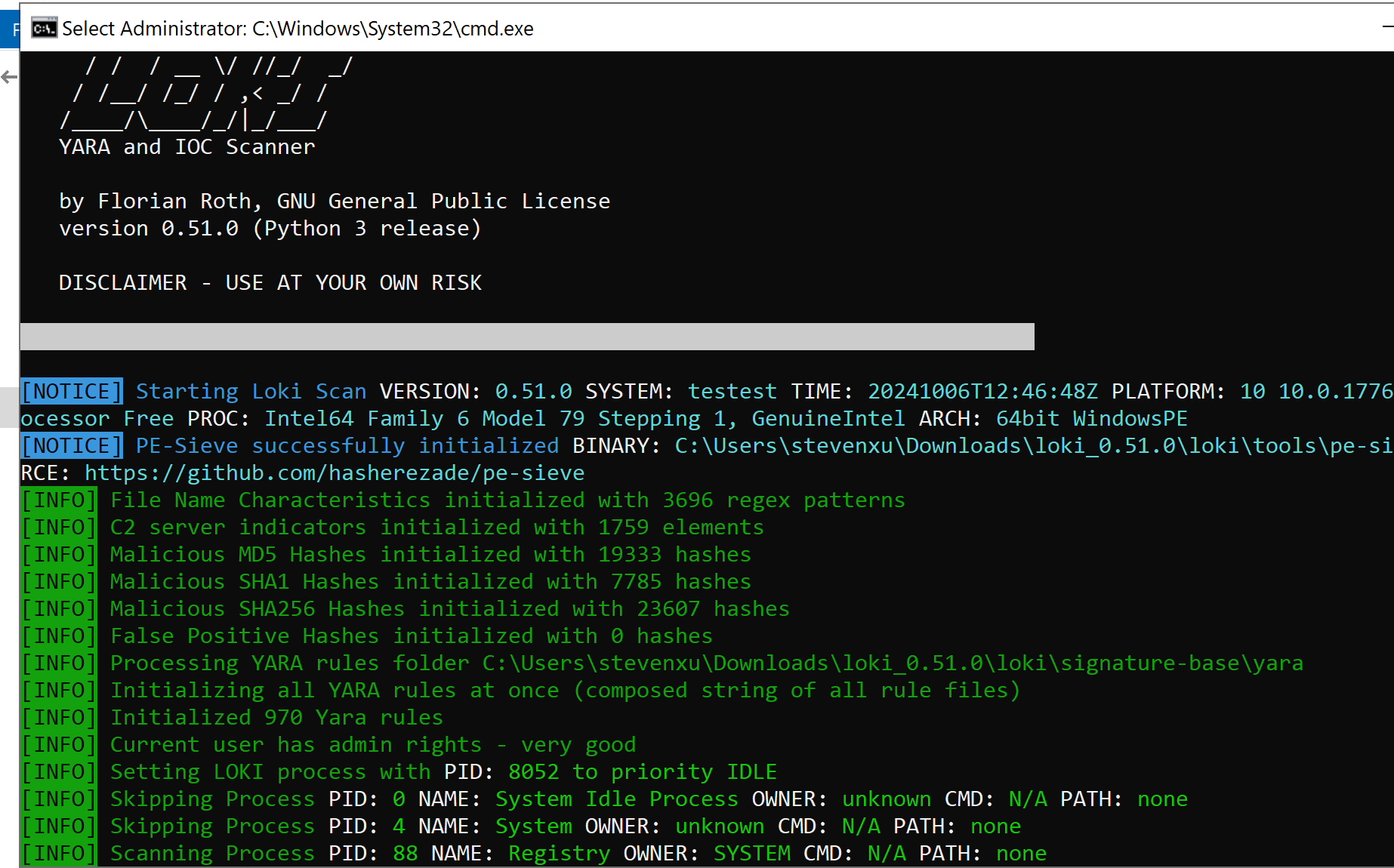 # 应急响应自动化脚本 1.上传工具包《windows应急响应工具包》 2.打开powershell执行 ``` # 使用DFIR 自动收集信息 cd Incident-Response-Powershell-main Powershell.exe -ExecutionPolicy Bypass .\DFIR-Script.ps1 # 进程分析:获取所有正在运行的进程 $processes = Get-Process $output = foreach ($process in $processes) { $processPath = $process.Path if ($processPath -ne $null) { $md5 = Get-FileHash -Path $processPath -Algorithm MD5 $sha256 = Get-FileHash -Path $processPath -Algorithm SHA256 $signature = Get-AuthenticodeSignature -FilePath $processPath $result = "进程名称: $($process.ProcessName)`r`n" $result += "路径: $processPath`r`n" $result += "MD5: $($md5.Hash)`r`n" $result += "SHA256: $($sha256.Hash)`r`n" if ($signature.Status -eq "Valid") { $result += "签名状态: 有效`r`n" $result += "签名算法: $($signature.SignerCertificate.SignatureType)`r`n" $result += "签名发布者: $($signature.SignerCertificate.Subject)`r`n" $result += "签名颁发者: $($signature.SignerCertificate.Issuer)`r`n" $result += "签名有效期: 从 $($signature.SignerCertificate.NotBefore) 到 $($signature.SignerCertificate.NotAfter)`r`n" } else { $result += "签名状态: 无效`r`n" } $result += "---------------------------------------------`r`n" $result } } $output | Out-File -FilePath "process_result.txt" # 网络分析:正在连接的端口和进程 $tcpConnections = Get-NetTCPConnection | Select-Object LocalAddress, LocalPort, RemoteAddress, RemotePort, State, OwningProcess $udpListeners = Get-NetUDPEndpoint | Select-Object LocalAddress, LocalPort, OwningProcess $connections = $tcpConnections + $udpListeners $output = @() foreach ($connection in $connections) { $processId = $connection.OwningProcess $process = Get-Process -Id $processId $output += [PSCustomObject]@{ LocalAddress = $connection.LocalAddress LocalPort = $connection.LocalPort RemoteAddress = $connection.RemoteAddress RemotePort = $connection.RemotePort State = $connection.State ProcessName = $process.ProcessName ProcessId = $process.Id } } $output | Export-Csv -Path "network_result.csv" -NoTypeInformation # DNS分析:DNS Cache $dnsCache = Get-DnsClientCache $dnsCache | Export-Csv -Path "dns_cache.csv" -NoTypeInformation ###################持久化分析 # 检查自启动程序 Write-Host "Checking Startup Programs:" $startupPrograms = Get-WmiObject Win32_StartupCommand | Select-Object Name, Command foreach ($program in $startupPrograms) { Write-Host "Name: $($program.Name), Command: $($program.Command)" } # 检查计划任务 Write-Host "Checking Scheduled Tasks:" $scheduledTasks = Get-ScheduledTask | Select-Object TaskName, TaskPath, State foreach ($task in $scheduledTasks) { Write-Host "TaskName: $($task.TaskName), TaskPath: $($task.TaskPath), State: $($task.State)" } # 检查注册表启动项 Write-Host "Checking Registry Run Keys:" $runKeys = Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run' foreach ($key in $runKeys.PSObject.Properties) { Write-Host "Name: $($key.Name), Value: $($key.Value)" } # 检查服务 Write-Host "Checking Windows Services:" $services = Get-Service | Select-Object DisplayName, StartType foreach ($service in $services) { Write-Host "DisplayName: $($service.DisplayName), StartType: $($service.StartType)" } # 检查持久化的WMI事件订阅 Write-Host "Checking WMI Event Subscriptions:" $eventFilters = Get-WmiObject __EventFilter | Select-Object Name, EventNamespace foreach ($filter in $eventFilters) { Write-Host "Name: $($filter.Name), EventNamespace: $($filter.EventNamespace)" } # 检查持久化的注册表项 Write-Host "Checking Persistence Registry Keys:" foreach ($key in $regKeys) { $regValues = Get-ItemProperty -Path $key foreach ($value in $regValues.PSObject.Properties) { Write-Host "Name: $($value.Name), Value: $($value.Value)" } } ``` # 参考资料 https://kqlquery.com/posts/incident-response-powershell-v2/ https://threathunterplaybook.com/intro.html https://zgao.top/%E4%BD%BF%E7%94%A8kape%E8%87%AA%E5%8A%A8%E5%8C%96%E9%87%87%E9%9B%86%E5%B9%B6%E5%88%86%E6%9E%90windows%E5%8F%96%E8%AF%81%E6%95%B0%E6%8D%AE/ https://mahim-firoj.medium.com/incident-response-and-threat-hunting-using-hayabusa-tool-383da273183a https://github.com/Psmths/windows-forensic-artifacts/tree/main https://medium.com/@rihanmujahid46/live-windows-forensics-using-powershell-and-sysinternals-c6997e869075 https://github.com/Bypass007/Emergency-Response-Notes 推荐 https://github.com/theLSA/emergency-response-checklist 推荐 https://github.com/Just-Hack-For-Fun/Windows-INCIDENT-RESPONSE-COOKBOOK NOP Team的wiidnows应急响应脚本 https://github.com/Psmths/windows-forensic-artifacts 推荐